How to Login to Your Trezor Hardware Wallet – Step by Step Guide
Introduction
Managing cryptocurrency requires a secure and reliable method to access your assets, and Trezor Hardware Wallet is one of the most trusted solutions available. Whether you’re a beginner or a seasoned crypto investor, knowing how to log in safely is essential. This guide will walk you through the process of logging into your Trezor device, ensuring your funds remain secure at all times.
Step 1: Setting Up Your Trezor Wallet
Before logging in, ensure your Trezor Hardware Wallet is properly set up. When you first receive your device, you will go through an initialization process where you create a PIN code and generate a recovery seed. The recovery seed is crucial—it is your only way to restore your wallet if your device is lost or damaged. Always store it securely offline, never digitally.
Step 2: Connecting Your Trezor Device
Plug your Trezor Wallet into your computer using the USB cable provided. You may need to visit the official Trezor Websiteto access the Trezor Bridge software, which allows your device to communicate securely with your browser. Trezor Bridge supports most browsers, including Chrome, Firefox, and Edge.
Step 3: Entering Your PIN Code
Once the Trezor interface is active, you will be prompted to enter your PIN. The Trezor screen displays a grid with randomized numbers, and your computer will show the corresponding empty grid. This randomization ensures that any keyloggers on your computer cannot capture your PIN. Carefully tap the numbers on your Trezor device according to your PIN sequence.
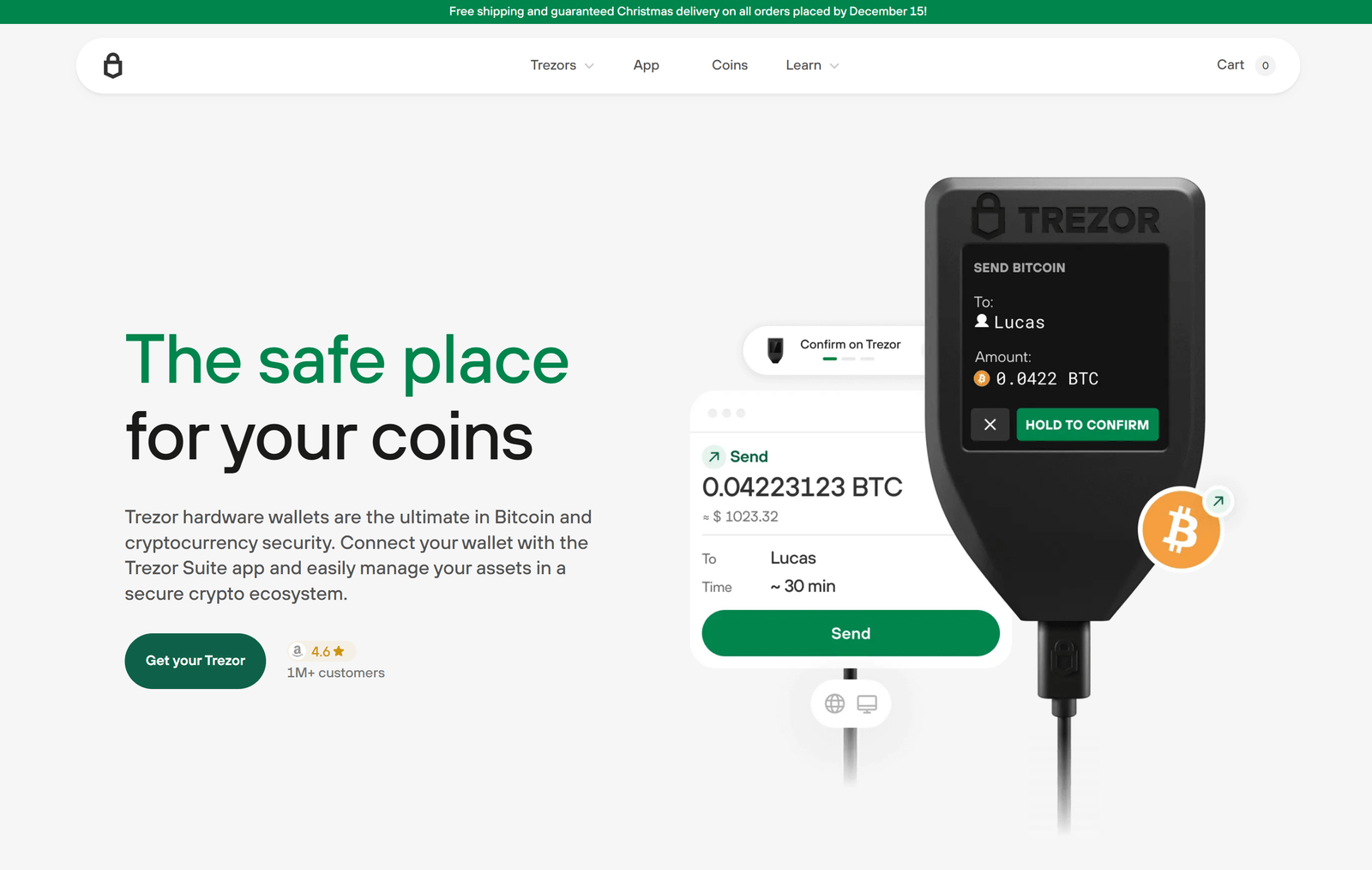
Step 4: Accessing Your Wallet
After entering the correct PIN, your Trezor Wallet dashboard will appear. Here you can view your crypto balances, send or receive funds, and manage multiple accounts. Trezor provides real-time transaction data and secure signing of transactions directly on the hardware, ensuring maximum safety.
Step 5: Logging Out Safely
Always remember to log out and disconnect your Trezor device after use. Your wallet remains secure only if you maintain proper device hygiene and never leave it connected unattended. This practice helps prevent unauthorized access and protects your investments from potential cyber threats.
Security Tips
- Never share your PIN or recovery seed.
- Use a passphrase for extra security on your Trezor device.
- Keep firmware updated to benefit from the latest security features.
Conclusion
Logging into your Trezor Hardware Wallet is simple but requires attention to security. By following this guide, you ensure safe and seamless access to your crypto assets. The combination of a hardware wallet, PIN, and recovery seed provides unmatched protection in today’s digital currency landscape.